
Disclaimer:
- This article is for informational proposes only
- Just like most information on the web, this article may contain outdated, inaccurate, or incomplete information.
Through the 2000s, most “browser specificity” boiled down to parsing the User-Agent header and a few passive signals like Accept-Language. Sites used this to serve different code paths to IE, Firefox, Safari, and later Chrome. Standards bodies and docs have long warned that UA sniffing is brittle and privacy-hostile, nudging developers toward feature detection instead.
As the platform grew, scripts began to actively query APIs to build higher-entropy “browser fingerprints”:
Canvas/WebGL: tiny off-screen drawings whose pixel-level differences reveal GPU/driver and font stacks. A 2014 Princeton/KU Leuven study documented canvas fingerprinting at scale and put the technique in the spotlight.
AudioContext: oscillators and filters can produce device-specific numerical “signatures,” observed in large web crawls.
Fonts & metrics: enumerating available fonts or measuring text layout adds more bits of entropy.
Battery Status (deprecated): once usable for short-term re-identification, it was curtailed/removed in major browsers over privacy concerns.
API-Level Integrity Verification
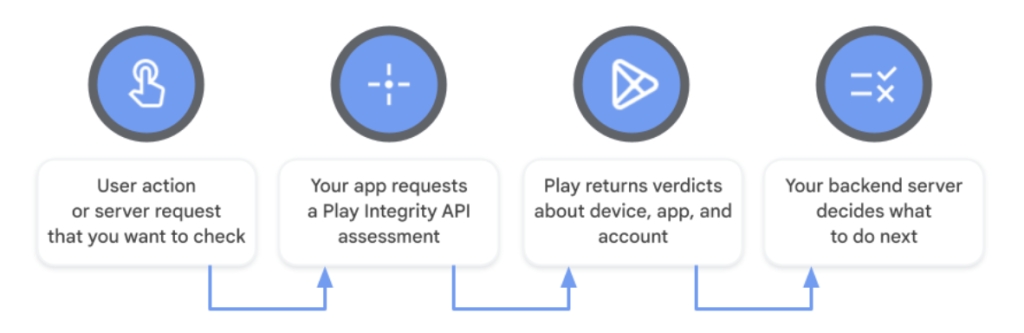
Source: Android Developers
On mobile, the ecosystem moved beyond fingerprints to attestation, cryptographic proofs that a request really comes from an untampered app on a certified Android device, not an Android Emulator.
Android SafetyNet/Play Integrity: Google deprecated SafetyNet and unified signals under the Play Integrity API, which lets an app request an encrypted integrity token and have its backend verify it before honoring sensitive actions. This is the mainstream pattern for “API-level verification” today.
Restrict your API key to your Android app by package name and the signing cert’s SHA-1. This prevents other apps from using your key even if it leaks.
Ask Play Integrity for a verdict during sensitive flows (account actions, purchases, high-value API calls).
Verify on your server: decrypt/validate the token and check verdict fields (e.g., device/app integrity) before calling downstream Google APIs or your own protected endpoints.
These two layers key restriction & attestation are complementary and Google’s docs walk through both.
Apple’s App Attest plays a similar role in iOS land, but that’s another article.
Chrome/Google’s New Browser-Level User Integrity Verification
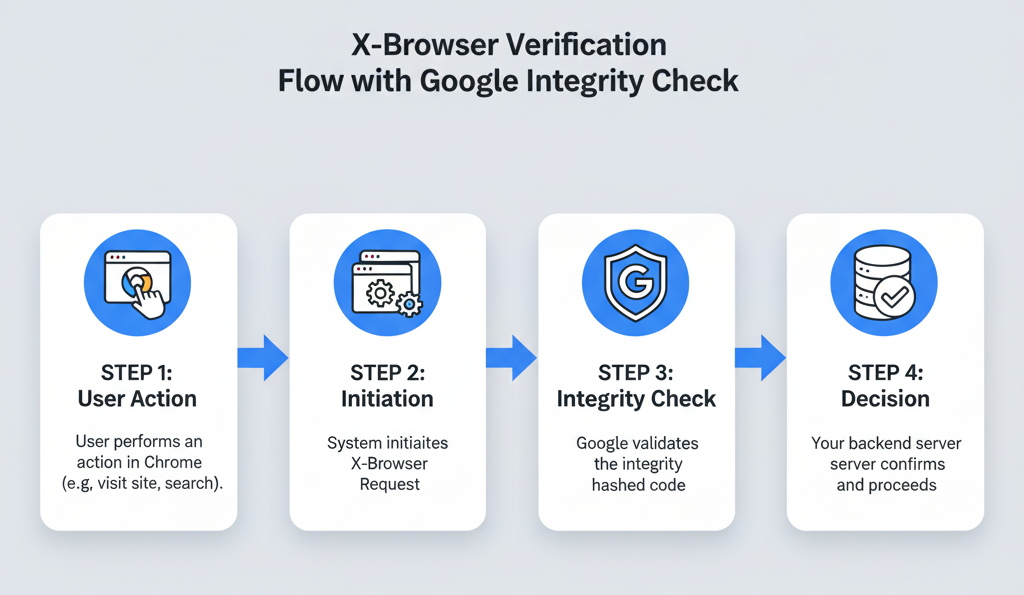
Multiple community posts noticed Chrome sending a cluster of undocumented new request headers (x-browser-validation, x-browser-channel), etc and speculated that the values act as an integrity hint (i.e., “is this really Chrome?”).

There’s a GitHub repo claiming to reverse-engineer the x-browser-validation value, and discussion threads on HN/Reddit where developers reported seeing the headers in the wild. Google hasn’t published official docs at the time of writing, and the exact purpose aren’t stated publicly, so treat these claims cautiously:
- Search & AI Mode Scraping
- Click manipulation (Given Google’s extensive use of fresh & historical user data in search)
- Gemini & Gemini in Chrome
Such a integrate is simply the differentiation between ‘spoofed’ versions of Chrome and the real, stable version, but it’s for one reason: bot detection.
Here’s how it works:
API_KEY + USER_AGENT
Google occasionally checks your specific Chrome API key relevant to your OS and matches it against the User-Agent. If there’s a match, everything is fine. If there’s no match or a mismatch, then X-Browser-Validation Header is not generated.
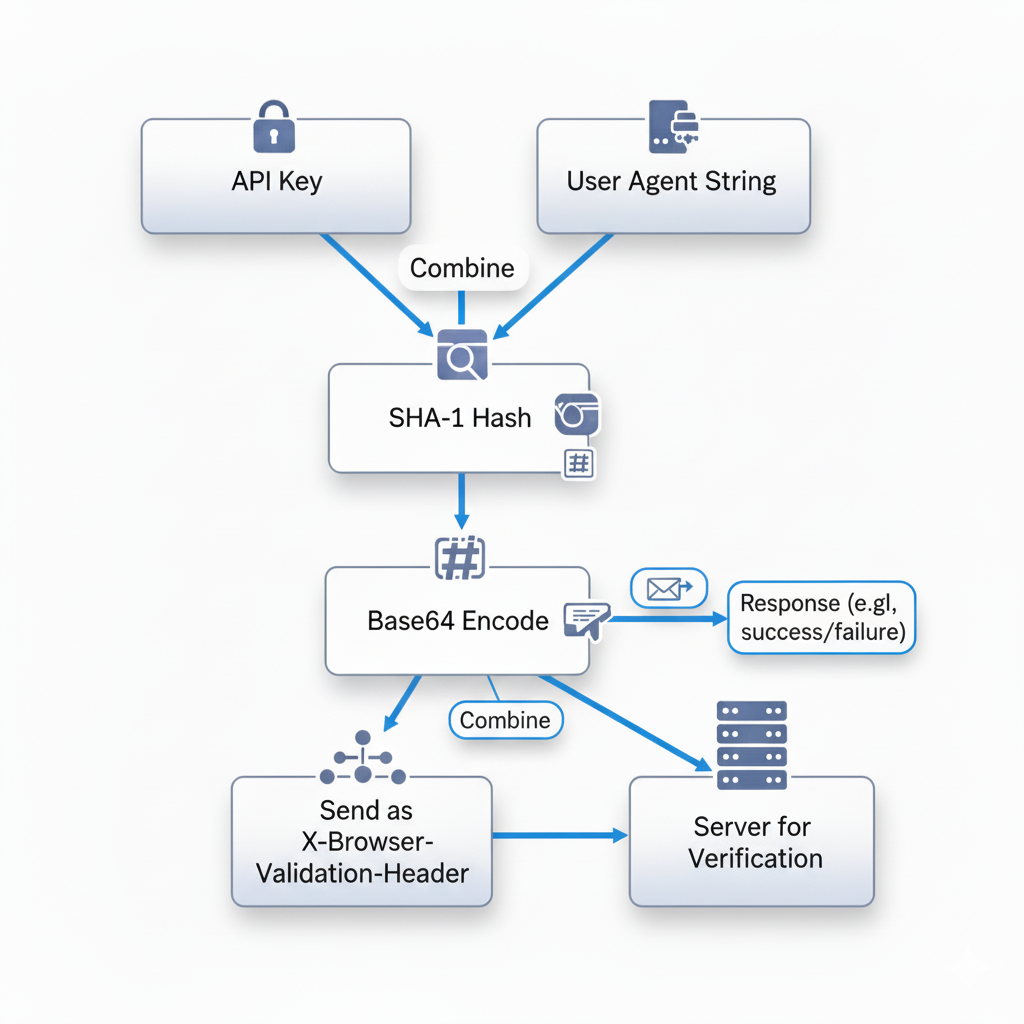
API Keys (Source the Github Repo):
Platform Default Key (found in Chrome binaries) Windows AIzaSyA2KlwBX3mkFo30om9LUFYQhpqLoa_BNhELinux AIzaSyBqJZh-7pA44blAaAkH6490hUFOwX0KCYMmacOS AIzaSyDr2UxVnv_U85AbhhY8XSHSIavUW0DC-sY
Credit to @dsekz on Gibhub for digging into Chrome binaries. I tried to find a link to @dsekz’s YouTube or website to promote him in this article, but couldn’t find any. So, feel free to subscribe to his GitHub repo, he shares mind-blowing discoveries and great insights!
Additionally, Google generates and analyzes a ‘Chrome consistency’ report via apps.googleusercontent.com, which measures these factors/values:
1- Device ID
2- Sync account ID
3- Mode
4- Signing Mode
Will Firefox, Edge, and Safari adopt browser-level verification methods?
This could be possible, with or without a partnership among all browsers, similar to how Google’s Safe Browsing API was created to provide a list of dangerous sites based on semi–real-time user data. The Safe Browsing API collects data from all major browsers, not just Chrome.
The partnership benefited all users, not just Chrome. However, there are some policies and challenges with such an idea:
- Safari on mobile, even through Chrome, doesn’t let Google collect data (as far as I know)
- Firefox and Google have historically had a love–hate relationship: Firefox replaced Google with Yahoo as the default search engine, then switched back to Google in 2017.
However, a common enemy in the age of AI could unite all browsers to find a solution.
At some point in the future, regulators may step in to force tech companies to find a way to distinguish AI users from human users. Even now, a measurable amount of the web’s traffic is bot.

Leave a Reply